


修改此文件("+"号为修改内容)
device/rockchip/common/BoardConfig.mkBOARD_BOOT_HEADER_VERSION ?= 2BOARD_MKBOOTIMG_ARGS :=BOARD_PREBUILT_DTBOIMAGE ?= $(TARGET_DEVICE_DIR)/dtbo.imgBOARD_ROCKCHIP_VIRTUAL_AB_ENABLE ?= false-BOARD_SELINUX_ENFORCING?=true+BOARD_SELINUX_ENFORCING?=false修改此文件("+"号为修改内容)
system/extras/su/su.cpp
void extract_uidgids(const char* uidgids, uid_t* uid, gid_t*gid, gid_t* gids, i}int main(int argc, char** argv) {- uid_t current_uid = getuid();- if (current_uid != AID_ROOT && current_uid != AID_SHELL) error(1, 0, "notallowed");+ //uid_t current_uid = getuid();+ //if (current_uid != AID_ROOT && current_uid != AID_SHELL) error(1, 0, "notallowed");给su文件默认授予root权限
修改此文件("+"号为修改内容)
system/core/libcutils/fs_config.cpp
staticconststructfs_path_configandroid_dirs[] = { { 00751, AID_ROOT, AID_SHELL, 0, "system/bin" }, { 00755, AID_ROOT, AID_ROOT, 0, "system/etc/ppp" }, { 00755, AID_ROOT, AID_SHELL, 0, "system/vendor" },- { 00750, AID_ROOT, AID_SHELL, 0, "system/xbin" },+ { 00755, AID_ROOT, AID_SHELL, 0, "system/xbin" }, { 00751, AID_ROOT, AID_SHELL, 0, "system/apex/*/bin" }, { 00751, AID_ROOT, AID_SHELL, 0, "system_ext/bin" }, { 00751, AID_ROOT, AID_SHELL, 0, "system_ext/apex/*/bin" },staticconststructfs_path_configandroid_files[] = {// the following two files are INTENTIONALLY set-uid, but they// are NOT included on user builds. { 06755, AID_ROOT, AID_ROOT, 0, "system/xbin/procmem" },- { 04750, AID_ROOT, AID_SHELL, 0, "system/xbin/su" },+ { 06755, AID_ROOT, AID_SHELL, 0, "system/xbin/su" },frameworks/base/core/jni/com_android_internal_os_Zygote.cppstatic void DropCapabilitiesBoundingSet(fail_fn_t fail_fn) {+/*for (int i = 0; prctl(PR_CAPBSET_READ, i, 0, 0, 0) >= 0; i++) {;if (prctl(PR_CAPBSET_DROP, i, 0, 0, 0) == -1) {if (errno == EINVAL) { ALOGE("prctl(PR_CAPBSET_DROP) failed with EINVAL. Please verify ""your kernel is compiled with file capabilities support"); } else { fail_fn(CREATE_ERROR("prctl(PR_CAPBSET_DROP, %d) failed: %s", i, strerror(errno))); } } }+ */}kernel-5.10/security/commoncap.cintcap_task_setnice(struct task_struct *p, int nice)staticintcap_prctl_drop(unsigned long cap){struct cred *new;+/* if (!ns_capable(current_user_ns(), CAP_SETPCAP)) return -EPERM; if (!cap_valid(cap)) return -EINVAL;-+*/new = prepare_creds();源码编译并验证固件是否ROOT
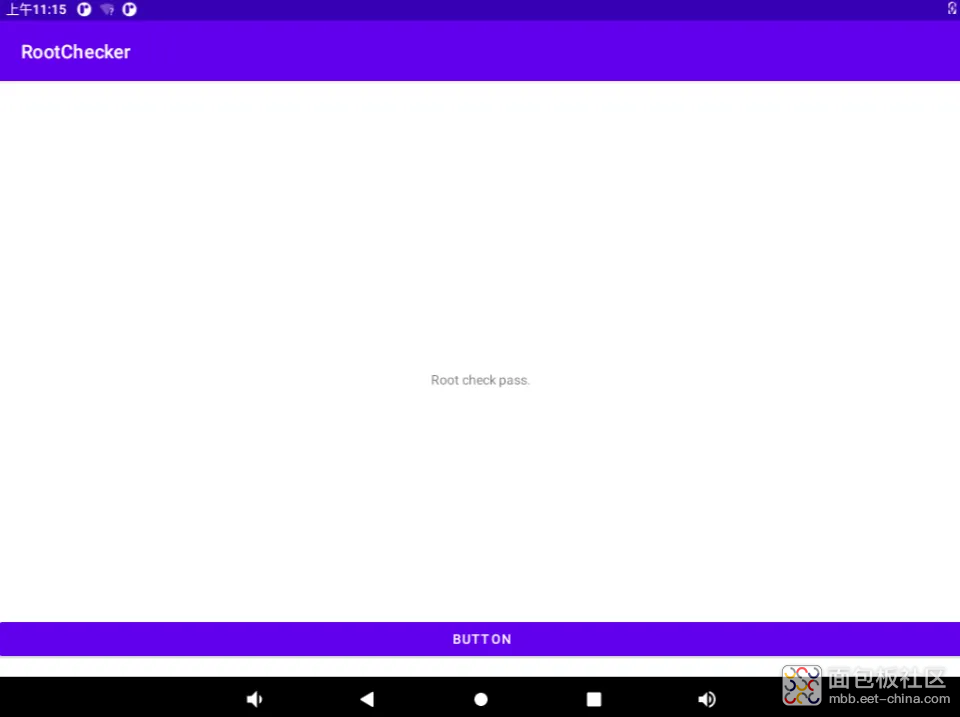
修改完上面三个步骤的文件后,重新编译内核和安卓源码,执行以下命令:
# make -j4
作者: Industio_触觉智能, 来源:面包板社区
链接: https://mbb.eet-china.com/blog/uid-me-4098392.html
版权声明:本文为博主原创,未经本人允许,禁止转载!
 /5
/5 
文章评论(0条评论)
登录后参与讨论